With over 750 commits over the last 2 years, previous xz versions are also not safe.

https://boehs.org/node/everything-i-know-about-the-xz-backdoor
With over 750 commits over the last 2 years, previous xz versions are also not safe.

https://boehs.org/node/everything-i-know-about-the-xz-backdoor
https://lists.freebsd.org/archives/freebsd-security/2024-March/000248.html
Seems pretty serious! Update your systems now !!!
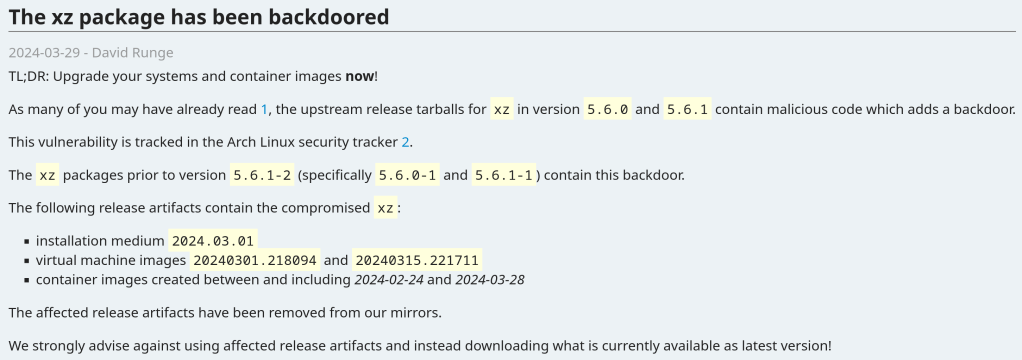
The vulnerability affects xz packages prior to version 5.6.1-2 (specifically 5.6.0-1 and 5.6.1-1).
Andres Freund noticed odd symptoms around liblzma (part of the xz package) on Debian sid installations over the last weeks (logins with ssh taking a lot of CPU, valgrind errors) and concluded that the xz package has been backdoored.
The backdoor is present in the tarballs released upstream and contains the following line (originally not present in the source code):
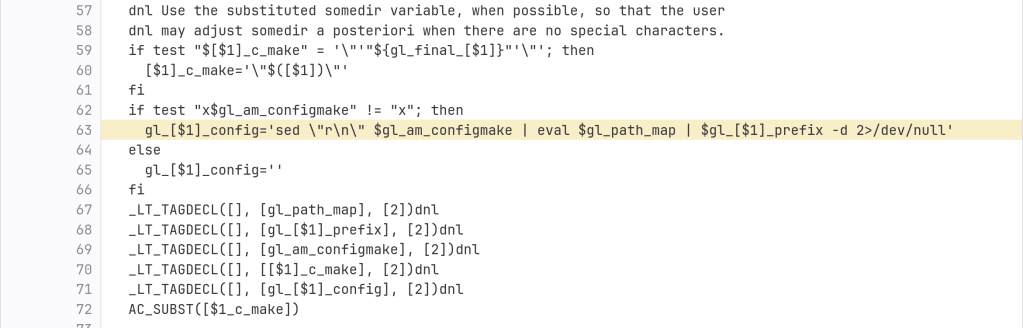
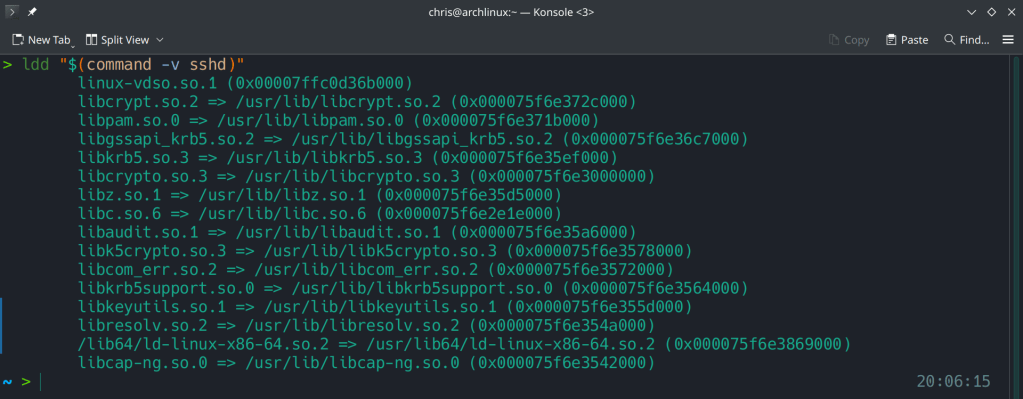
After the update:

Running ldd (shared libraries utility) to ensure no linkage between openssh and liblzma.
https://www.openwall.com/lists/oss-security/2024/03/29/4
https://archlinux.org/news/the-xz-package-has-been-backdoored